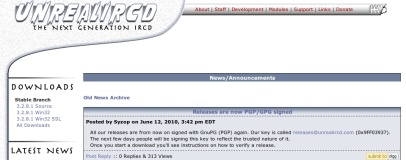
A nasty backdoor that found its way into the source code of a popular IRC server application has been rooted out - and has provided a wake-up call to the Linux world regarding security best practices.
Although far, far rarer than Windows malware, attacks against Linux-based operating systems are definitely out there - and while security features built in to the operating system, such as commonly running as a non-administrative user and the requirement to mark files as executable before they will run, make Linux-based operating systems a much harder target, there are those who will continue to try.
It is one such attacker who managed - somehow - to insert a backdoor Trojan into the source code for the UnrealIRCd package - an Internet Relay Chat daemon for Linux. According to Sophos' Chester Wisniewski, the backdoor has been present in the source code since as far back as November 2009 - providing ne'er-do-wells with an easy entry point into affected systems.
The common cry of "I don't need anti-virus software, I'm on Linux," might still be true - despite Wisniewski claiming that his company's products would have protected against the backdoor - but this major security breach highlights the requirement to stick to the rules of industry best practice no matter how secure your operating system might be.
While the users who downloaded the code might hold some culpability for not checking their sources, it's the project's administrators who should hang their heads: a combination of not checking their repositories for unauthorised changes, a failure to publish checksums or digital signatures for the code which would have highlighted the changes, and providing the tainted code to mirrors again without checksums have left the project's users open to attack for months.
Thankfully, the team have now wised up: with the Trojan removed and the code base cleaned, all future releases are digitally signed to prevent tampering - although for the project's users the move could well be too little, too late.
Are you shocked to see a Linux app fall prey to a backdoor Trojan, or is this the sort of thing you expect when package maintainers fail to do their job properly? Could Linux be mainstream enough now to require anti-virus software? Share your thoughts over in the forums.
Although far, far rarer than Windows malware, attacks against Linux-based operating systems are definitely out there - and while security features built in to the operating system, such as commonly running as a non-administrative user and the requirement to mark files as executable before they will run, make Linux-based operating systems a much harder target, there are those who will continue to try.
It is one such attacker who managed - somehow - to insert a backdoor Trojan into the source code for the UnrealIRCd package - an Internet Relay Chat daemon for Linux. According to Sophos' Chester Wisniewski, the backdoor has been present in the source code since as far back as November 2009 - providing ne'er-do-wells with an easy entry point into affected systems.
The common cry of "I don't need anti-virus software, I'm on Linux," might still be true - despite Wisniewski claiming that his company's products would have protected against the backdoor - but this major security breach highlights the requirement to stick to the rules of industry best practice no matter how secure your operating system might be.
While the users who downloaded the code might hold some culpability for not checking their sources, it's the project's administrators who should hang their heads: a combination of not checking their repositories for unauthorised changes, a failure to publish checksums or digital signatures for the code which would have highlighted the changes, and providing the tainted code to mirrors again without checksums have left the project's users open to attack for months.
Thankfully, the team have now wised up: with the Trojan removed and the code base cleaned, all future releases are digitally signed to prevent tampering - although for the project's users the move could well be too little, too late.
Are you shocked to see a Linux app fall prey to a backdoor Trojan, or is this the sort of thing you expect when package maintainers fail to do their job properly? Could Linux be mainstream enough now to require anti-virus software? Share your thoughts over in the forums.

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04







Want to comment? Please log in.